Cybersecurity consulting and engineering
Our Offerings
CyberVault’s consulting and engineering services are built on a simple belief: effective cybersecurity starts with understanding how an organization actually operates. Not how a framework says it should operate, not how a tool vendor markets it—but how people work, how decisions are made, and how technology is really used day to day. Our goal is to give organizations a clear, honest view of their current security posture and a practical path forward that aligns with real business priorities. Rather than delivering abstract assessments or one-size-fits-all recommendations, CyberVault focuses on why gaps exist, how they create risk, and what can realistically be done to address them. This approach allows leadership and technical teams to make informed decisions, prioritize investments, and strengthen security without unnecessary complexity or disruption.
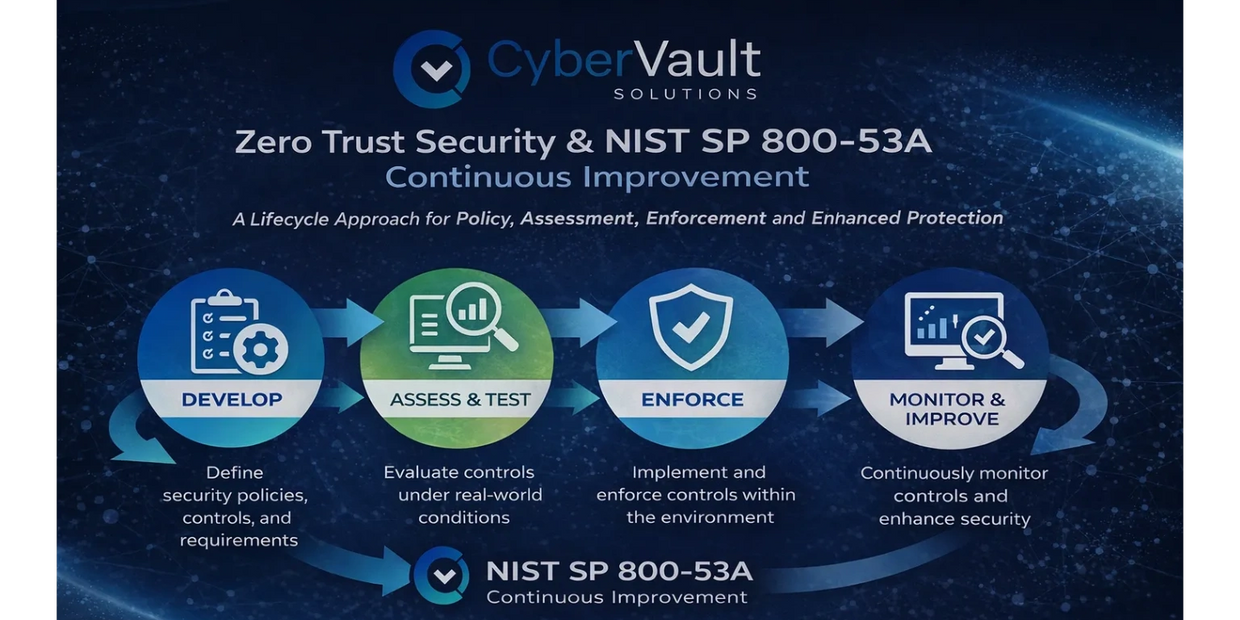
Zero Trust as a Strategy, not a CheckboA foundational element of our consulting approach is Zero Trust—but not as a buzzword or a standalone assessment. CyberVault treats Zero Trust as a long-term strategy and cultural shift, not a single project or technology implementation. We align our work with CISA’s Zero Trust Maturity Model, using it as a guide to help organizations understand where they are today and how to progress incrementally over time.Zero Trust, when implemented correctly, touches people, processes, and technology. It requires changes in how access is granted, how trust is evaluated, how users and devices are monitored, and how data is protected. More importantly, it requires a mindset shift—from implicit trust to continuous verification. CyberVault helps organizations internalize this shift by embedding Zero Trust principles into everyday operations rather than treating them as a separate initiative. Our evaluations look closely at identity and access controls, device posture, application access, data protection practices, and visibility across the environment. We examine how these elements function together under real conditions and how attackers might realistically exploit weaknesses. This ensures Zero Trust becomes a living practice—not a theoretical model.
Aligning to the Right Frameworks—Based on Your Needs
No two organizations face the same risks, regulatory pressures, or operational realities. That’s why CyberVault does not force clients into a single framework or methodology. Instead, we align security programs to the standards that make sense for the organization’s size, industry, and obligations. Depending on client needs, our work may align with methodologies such as NIST, ISO 27001, CIS Controls, SOC 2, CMMC, HIPAA, or GDPR. These frameworks are used as reference points, not rigid checklists. Our focus is on ensuring policies, controls, and governance structures are practical, enforceable, and understood by the people responsible for using them. CyberVault pays close attention to whether security processes are actually followed, whether documentation reflects reality, and whether controls are effective in practice—not just compliant on paper. Where gaps exist, we provide guidance rooted in proven methodologies and real-world experience, helping organizations strengthen security without creating unnecessary overhead.
People, Process, and Technology—Working Together
True security maturity doesn’t come from tools alone. It comes from the alignment of people, processes, and technology. CyberVault evaluates how these elements interact across the organization, identifying where breakdowns occur and where improvements will have the greatest impact.From a people perspective, we assess roles, responsibilities, and decision-making authority. From a process standpoint, we examine workflows such as access provisioning, incident escalation, change management, and vendor oversight. From a technology angle, we evaluate how systems are configured, monitored, and integrated. This holistic view allows us to surface risks that are often missed when assessments focus too narrowly on one area. Our approach helps organizations understand not just what needs to change, but whythose changes matter and how to implement them sustainably.
A Clear Path Forward—Without Overengineering
CyberVault’s consulting and engineering services are designed to bring clarity, not confusion. By combining strategic assessment with technical insight, we help organizations identify their most pressing risks and take measured, meaningful steps to reduce them. This ensures security improvements are aligned with business goals, budget realities, and operational constraints. Ultimately, our role is to act as a trusted partner—helping organizations build security programs that are resilient, defensible, and adaptable as threats and business needs evolve. We don’t just assess environments; we help organizations move forward with confidence.
Learn More
Zero Trust isn’t a product—it’s a strategy and a cultural shift. Explore how CyberVault aligns proven frameworks like NIST and CISA with real-world operations to help organizations build security programs that actually work.
This website uses cookies.
We use cookies to analyze website traffic and optimize your website experience. By accepting our use of cookies, your data will be aggregated with all other user data.

How are you preparing to achieve compliance?
The Office of Management and Budget (OMB) mandates Federal agencies to meet specific Zero Trust goals by the close of Fiscal Year 2024. Wondering how to ensure compliance? Let us guide you through seamless preparation.
